6 Safe Ways to Track My Wife’s Phone
The reason why you want to start tracking your wife's phone is due to mistrust. Other times, you may also want to protect her...
How to do Cloud Penetration Testing: A Complete Guide
Cloud penetration testing is a process that involves assessing the security of cloud services. Cloud computing has become increasingly popular and widespread over the...
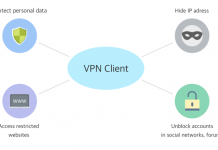
Reasons Why You Need a Good VPN Software
Recently, many resources are writing about VPN-services and anonymizers. The developers of the Opera browser not only released a free application for using VPN...
SMS Software for Clinics, Beauty Salons And Gyms
Today, when every person in the world has at least one smartphone and some have more than one mobile device, there is a logical...
Top 7 Phone Tracking Apps That You Can’t Miss In 2019
Kids today feel that just because they have mobile phones in their pockets all the time, they can do anything. But is that really...
‘Game of Thrones: The 8-bit Game’ is released
Game of Thrones fans desperately twiddling their thumbs until Season 4 starts next year (or until the next book is finally published) will be...
3 Reasons to Hide Your IP Address
There are many reasons why you might want to change your IP address. But most of them can be linked back to three main...
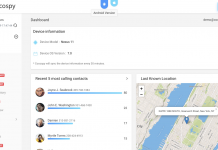
Reasons Why an Employer Needs a Good Android and iPhone Spy Software
Information is one of the most protected things in any
organization. That is because, in the wrong hands, certain information can lead
to the end of...
Google introduces new search algorithm, ‘Hummingbird’
On 27 September 2013 Google marked its 15th birthday, and with it its latest search algorithm. Google Hummingbird (which was actually quietly rolled out...
How to connect remotely to your PC
Have you ever, for some reason or another, needed to access your computer at home while you were at work? Maybe for some photos,...